According to the usage statistics of user application from Microsoft, 60% of the time people spend on the PC is within the web browser. Google Chrome is a cross-platform web browser developed by Google based on...
Hotspots—what are they, where are they, and how can you connect to them while protecting your privacy and security? If you’ve ever tried to answer an email or surf the Internet from your mobile device i...
Wireless communications have been expanding globally at an exponential rate. The latest imbedded version of mobile networking technology is called 4G (fourth generation), and the next version (called 5G –...
The company did not specify how many employees in total were affected. Lacework had reported having more than 1,000 employees in March, following a $1.3 billion funding round at an $8.3 billion valuation in Nov...
As the Christmas holiday continues to draw closer daily, packed with so much excitement in view, Google is about to make the season even more exciting with a number of new value-added features to Android phones...
Over the past few years, smartphones have evolved a lot. Apart from making calls, smartphones are nowadays utilized for various different purposes like browsing the web, watching videos, playing games, etc. So,...
10 useful tech tips you’ll use over and over. Everybody loves a cool trick such as phone case cleaning tips, . No matter how well we know an app or program, there’s almost always some shortcut we never learned....
“That’s a nice business you’ve got. It would be a shame if anything was to happen to it!” That, in a nutshell, is the classic gangster’s extortion pitch: fleecing victims for their hard-earned money by threaten...
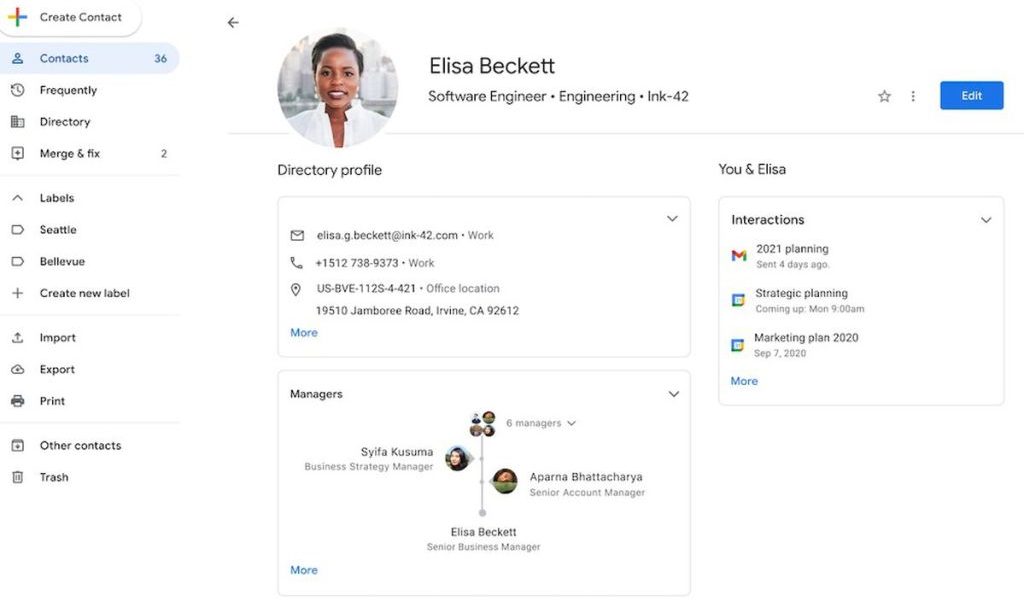
Google has revealed details about the Circle-style — an extra piece of information that gives a new user experience about Google Contact. According to the tech company, this extra information will mostly be use...
Did you know that more Billion was lost to card fraud worldwide every year since 2018. Also the Nilson reported that global card losses are expected to exceed $35 billion in the year 2020. This articles show 5...