Edge computing is a means of optimizing data processing in cloud-based computing systems by doing it closer to the data source at the network’s edge. Using edge computing technology has a number of advantages, including:
- Bringing high-bandwidth material far closer to the user.
- Assisting in the development of future network infrastructure.
- Providing assistance with latency issues.
Much of the high-performance processing that used to be done at the cloud’s core, such as data analysis, is now possible with certain types of network infrastructure. The edge, as seen in the diagram below, aids real-time data processing closer to the source or even on-premises.
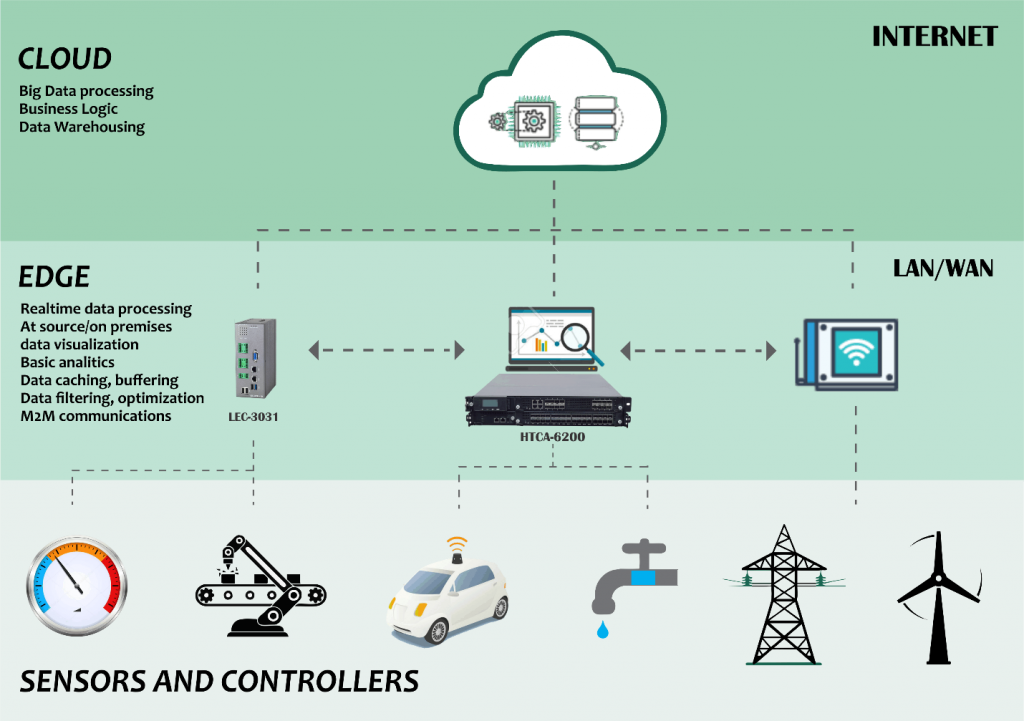

All of the data from Internet of Things sensors and controllers, such as cobots, smart vehicles, smart industry, and more, does not need to be delivered to the cloud directly. Sending massive amounts of data to servers all around the world for processing would take a long time. All of that data may be analyzed, buffered, and cached by these edge computing devices.
Edge Computing Technologies
Edge Computing with Multiple Access
Multi-access Edge Computing, also known as Mobile Edge Computing (MEC), is a network design that allows computational and storage resources to be placed within the radio access network (RAN). The MEC aids in improving network efficiency and content delivery to end-users. This gadget can accomplish so by adapting to the load on the radio link, improving network efficiency and lowering the demand.
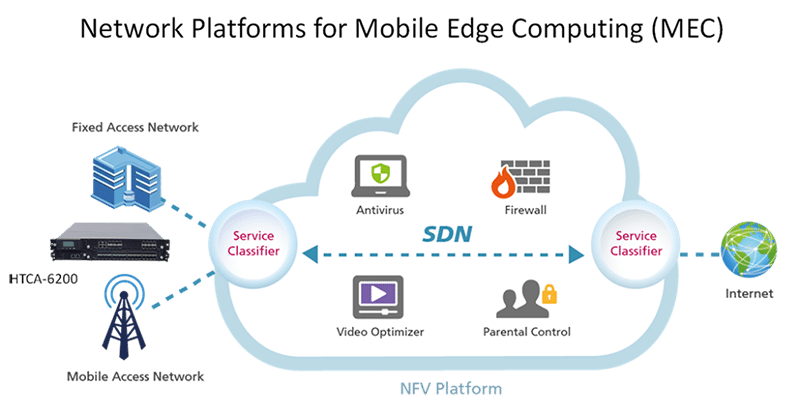

Because network needs are expected to rise dramatically as more IoT and 5G-enabled technologies and devices are created, mobile edge computing allows operators to better manage traffic and resource demands. It also aids in the establishment of future intelligent and next-generation networks’ foundations. Improved location, augmented reality, and Internet of Things services might all be supported by mobile edge computing.
Fog Computing
A decentralized computer infrastructure is referred to as fog computing, fog networking, or simply “fogging.” It brings cloud computing (data centers) to the network’s edge while also putting data, compute, storage, and applications in the most logical and efficient location possible. This position occurs between the cloud and the data source, and is also referred to as being “out in the fog.”
Fog nodes connect edge devices to the cloud, as depicted in the diagram below. These nodes are fog computing entities that have the ability to process and sense data.


Fog computing aims to extend cloud computing and services to the network’s edge while also attempting to limit the amount of data sent to the cloud for processing, analysis, and storage. Data from IoT sensors and other devices is typically transferred to the cloud for analysis and processing.
Cloudlets
Cloudlets are small-scale, mobility-enhanced cloud data centers that sit at the network’s edge.
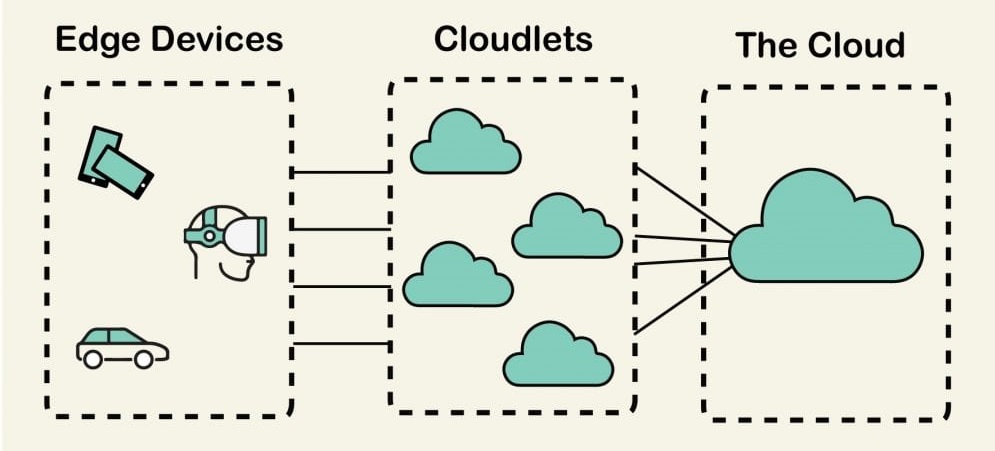

Cloudlets are designed to improve resource-intensive and interactive mobile apps by delivering more competent computing resources with lower latency to mobile devices in close proximity. Cloudlets were created to serve resource-intensive applications like augmented reality, machine learning, speech recognition, and language processing while 5G networks loom on the horizon.
Due to the increasing demand that will accompany the launch of 5G networks, Cloudlets will give the necessary help.
Cloud of Things
The concept of the cloud of things is still in its infancy, but it holds a lot of potential. All processing power is obtained from the extreme edge, at the end-user, in a Cloud of Things.
We all have powerful technologies in our hands, such as smartphones and Internet of Things (IoT) devices in our homes. These tools are frequently underutilized. Although the computing power of IoT devices is still limited, many modern mobile phones are quite powerful.
These devices could be orchestrated to provide edge cloud services. A car going through traffic, for example, might transmit traffic warning notifications to others and try to re-arrange other routes without the user’s participation. Mobile or IoT devices could be used to give cloud services right at the edge.
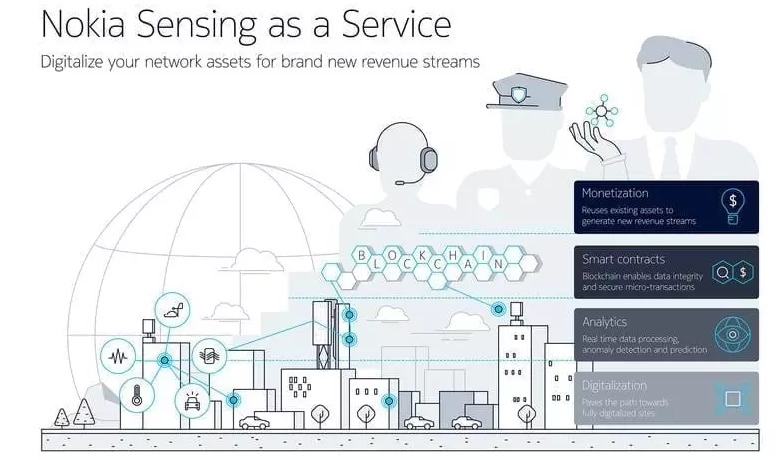
There are new CoT concepts such as Nokia’s Sensing-as-a-Service (shown below), which employs a pool of existing edge sensing technology that acts as cloud agents and is placed extremely close to the edge to operate as cloud agents.

Benefits of edge computing
Autonomy: Edge computing is beneficial in situations when connectivity is intermittent or bandwidth is limited due to environmental factors. Oil rigs, ships at sea, rural farms, and other remote settings, such as a rainforest or desert, are examples. Edge computing performs computations on the spot, sometimes on the edge device itself, such as water quality sensors on water purifiers in rural villages, and can save data to send to a central location only when connectivity is available.
Data sovereignty: It’s not merely a technological issue when it comes to moving massive amounts of data. The movement of data across national and regional borders can exacerbate data security, privacy, and other legal concerns. Edge computing can be used to retain data close to its source while being compliant with current data sovereignty regulations, such as the GDPR, which regulates how data should be stored, processed, and exposed in the European Union.
Edge security: Finally, edge computing provides a new way to implement and maintain data security. Despite the fact that cloud providers offer IoT services and specialize in complicated analysis, businesses are still concerned about data security after it leaves the edge and travels back to the cloud or data center. By deploying computing at the edge, any data traveling over the network back to the cloud or data center may be encrypted, and the edge deployment itself can be protected against hackers and other malicious actions — even if IoT device security is still lacking.
Challenges of edge computing
Data lifecycles: The problem with today’s data glut is that so much of it is useless; most of the data used in real-time analytics is short-term data that isn’t kept for long periods of time. Following the completion of analyses, a company must determine which data to keep and which to delete. Furthermore, the data that is kept must be protected in compliance with company and regulatory rules.
Connectivity: Although edge computing bypasses common network constraints, even the most tolerant edge deployments will require some amount of connectivity. It’s vital to plan an edge deployment that can handle sporadic or poor connectivity, as well as what occurs when connectivity is lost.
Limited capability: The diversity and quantity of resources and services that cloud computing delivers to edge or fog computing is part of the attractiveness. Even a large edge computing deployment serves a specified function at a pre-determined scale with restricted resources and few services, but the scope and purpose of the edge deployment must be explicitly stated.
Security: Because Internet of Things devices are notoriously insecure, it’s critical to plan an edge computing deployment that prioritizes proper device management, such as policy-driven configuration enforcement, as well as security in computing and storage resources, such as software patching and updates, with a focus on data encryption at rest and in flight.