According to the usage statistics of user application from Microsoft, 60% of the time people spend on the PC is within the web browser. Google Chrome is a cross-platform web browser developed by Google based on...
Hotspots—what are they, where are they, and how can you connect to them while protecting your privacy and security? If you’ve ever tried to answer an email or surf the Internet from your mobile device i...
Wireless communications have been expanding globally at an exponential rate. The latest imbedded version of mobile networking technology is called 4G (fourth generation), and the next version (called 5G –...
Anyone who has been to a cyber cafe would word the cafe’s software program and, take note, that an individual’s laptop is linked to the staff’s computer. One issue of Cafe Management is being capable to oversee...
As the Christmas holiday continues to draw closer daily, packed with so much excitement in view, Google is about to make the season even more exciting with a number of new value-added features to Android phones...
Tech evangelists habitually brim with enthusiasm over artificial intelligence’s potential to transform our lives, and the crowds at this year’s Web Summit were no exception. Here are five uses for AI showcased...
Over the past few years, smartphones have evolved a lot. Apart from making calls, smartphones are nowadays utilized for various different purposes like browsing the web, watching videos, playing games, etc. So,...
Social media giant Facebook has decided it’s time for change — by changing its name. But before you think that you’ll have to log in to some different website, it’s only the name of the company that’s changing,...
“That’s a nice business you’ve got. It would be a shame if anything was to happen to it!” That, in a nutshell, is the classic gangster’s extortion pitch: fleecing victims for their hard-earned money by threaten...
Microsoft had on Tuesday, the 31st of August 2021 intimated the public its plans to roll out Windows 11 on the 5th of October 2021, in a free upgrade of its operating system available for hardware that works wi...
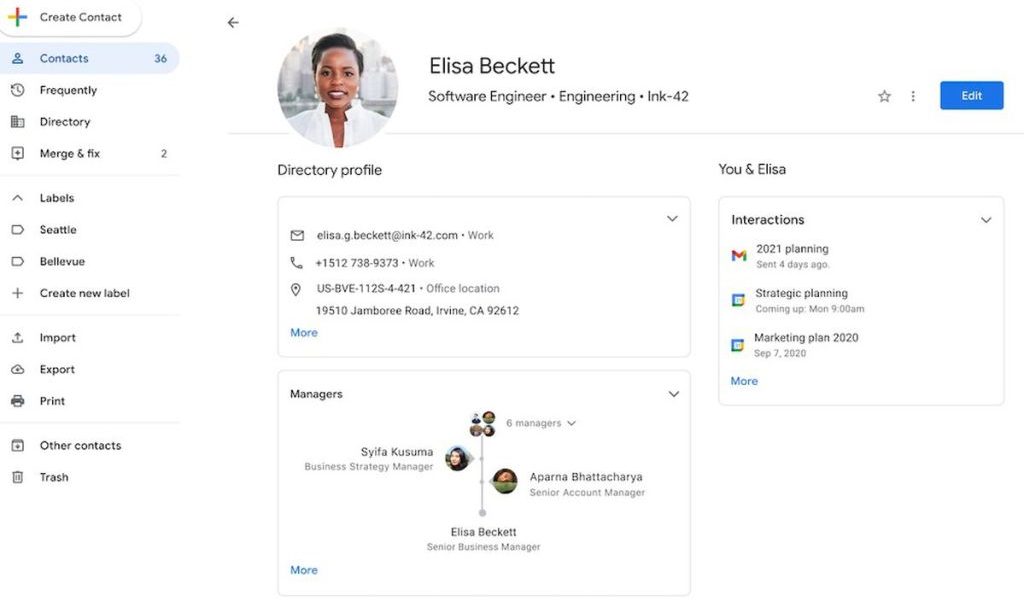
Google has revealed details about the Circle-style — an extra piece of information that gives a new user experience about Google Contact. According to the tech company, this extra information will mostly be use...
Emerging Technology Threats – Adware What do you understand by the word Adware – Adware, or advertising-supported software, is malicious software that displays unwanted advertisements on your computer. ...