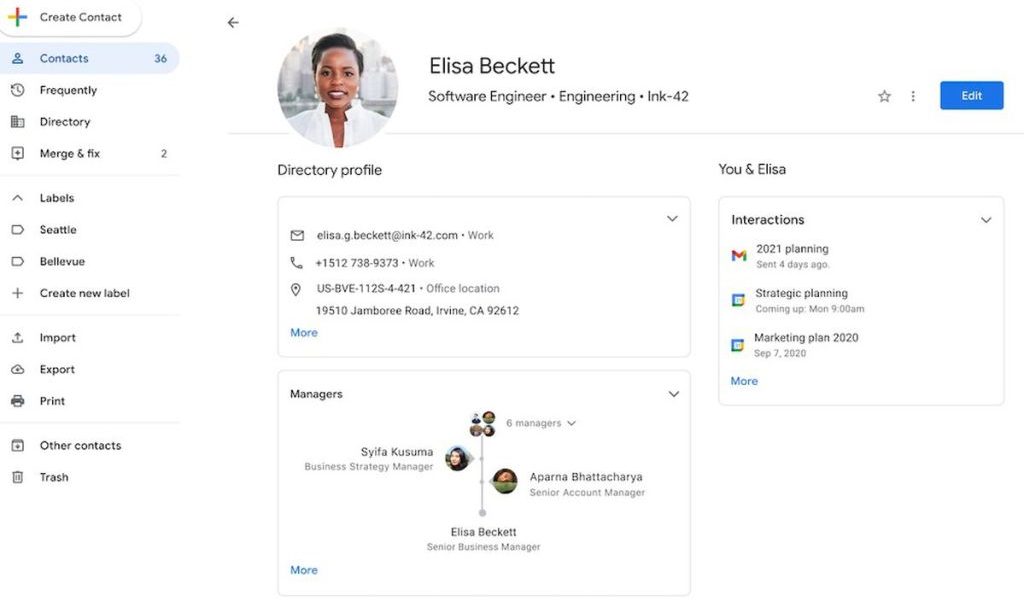
Google has revealed details about the Circle-style — an extra piece of information that gives a new user experience about Google Contact. According to the tech company, this extra information will mostly be use...
Create a folder for Control Panel Shortcuts. This is a great hack for those who need to change system settings at regular intervals and waste their time in finding those settings. Simply create a folder at the...
Minister of Communication and Digital Economy, Isa Pantami, has warned that unless proactive steps are taken to protect the nation’s critical infrastructure and assets, Nigeria could be exposed to worse cyber a...
Artificial intelligence (AI) cannot be the inventor of new patents, the UK Court of Appeal has ruled. Patents assign the ownership of a new invention to its creator. At its core, the argument is a...
A trainer according to Cambridge English Dictionary is a person who teaches skills to people and prepares them for a job. In simple term, a professional trainer is a teacher who works in a corporate setting to ...
Sophos is a security system that protects your privacy and family security. It’s also an enterprise grade cybersecurity for organisations Sophos offers three solutions: Sophos Endpoint Sophos MTR Sophos Firewa...
What you need to know about Firewall! The Internet has made much information available to the average computer user at home, in business, and education. For many people, access to this information is no longer ...
Edge computing is a means of optimizing data processing in cloud-based computing systems by doing it closer to the data source at the network’s edge. Using edge computing technology has a number of advantages, ...
A VPN is defined as a “Virtual Private Network” and it describes the ability to provide a secure connection when you use an open network. A VPN encrypts all your internet traffic and hides your identity online....
Cryptocurrencies are regularly featured in the headlines, arranging the highest and most extreme wildlife trips. When the millennium-based anti-establishment base was heated economically in 2008, many instituti...
Cloud Infrastructures promote environmental pro-activity by powering virtual services rather than physical goods and hardware, reducing paper waste, improving energy efficiency, and reducing commuter-related po...
EMERGING TECHNOLOGY THREAT – PHISHING The invention of information and communication technology (ICTs) has invaded our lives, be it business, personal or recreational purposes. We rely heavily on the Internet f...